Sophos
Central Intercept X for Server
Central Intercept X for Server
Couldn't load pickup availability
Server Workload Protection
High-impact protection with low impact on performance
for on-premise, data center, and cloud workloads.
Server Workload Protection Features
Cloud Native Security
Advanced protection for cloud hosts and containers, optimized for DevSecOps workflows.
Secure your Windows and Linux deployments whether they are in the multi-cloud, on-premises, virtual or a mix of them all. Deployment across mixed setups is straightforward, using a singular agent. Policies can also be applied to all servers even in mixed environments, making deployment, configuration and management quick and easy.
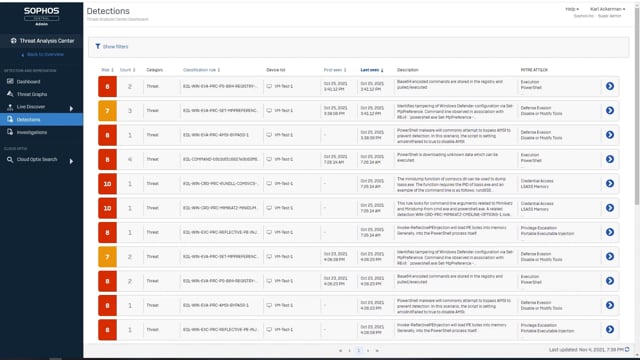
Extended Detection and Response (XDR)

Sophos Intercept X Advanced for Server with XDR is the industry’s only XDR solution that synchronizes native endpoint, server, firewall, email, cloud and O365 security. Get a holistic view of your organization’s environment with the richest data set and deep analysis for threat detection, investigation and response for both dedicated SOC teams and IT admins.
Managed Detection and Response

Sophos Managed Detection and Response (MDR) provides 24/7 threat hunting, detection, and response capabilities delivered by an expert team as a fully-managed service. Sophos MDR fuses machine learning technology and expert analysis for improved threat hunting and detection, deeper investigation of alerts, and targeted actions to eliminate threats with speed and precision. Unlike other services, the Sophos MDR team goes beyond simply notifying you of attacks or suspicious behaviors, and takes targeted actions on your behalf to neutralize even the most sophisticated and complex threats.
Deep Learning Technology
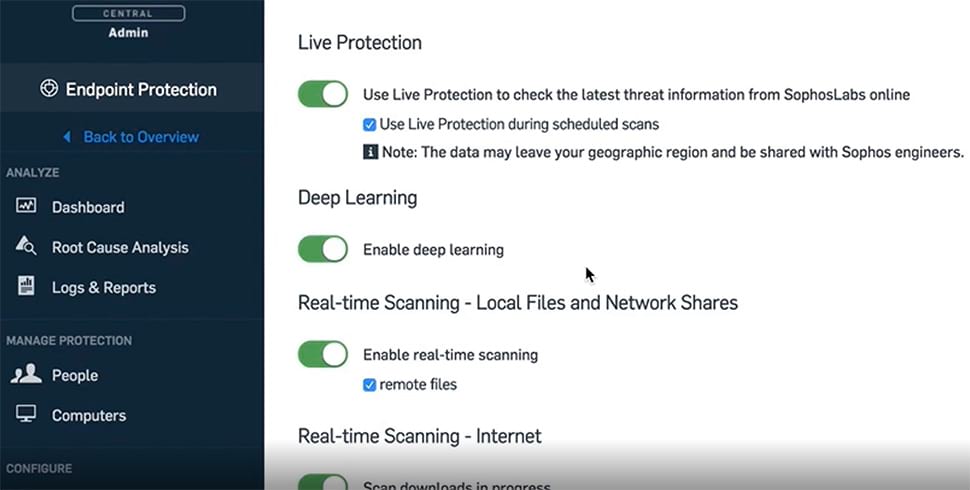
By integrating deep learning, an advanced form of machine learning, Intercept X for Server is changing server security from a reactive to a predictive approach to protect against both known and never-seen-before threats. While many products claim to have machine learning, not all machine learning is created equally. Deep learning has consistently outperformed other machine learning models for malware detection.
Exploit Prevention
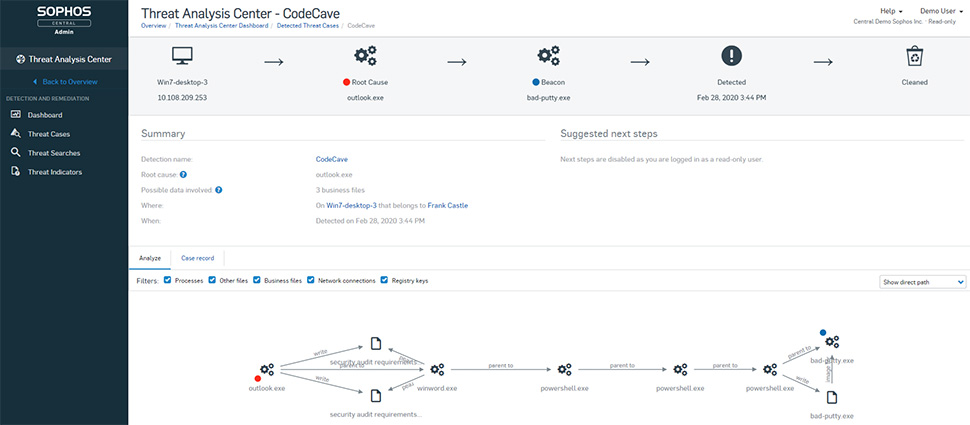
Exploit prevention stops the techniques used in file-less, malware-less, and exploit-based attacks. While there are millions of pieces of malware in existence, and thousands of software vulnerabilities waiting to be exploited, there are only handful of exploit techniques attackers rely on as part of the attack chain – and by taking away the key tools hackers love to use, Intercept X stops zero-day attacks before they can get started.
Anti-Ransomware
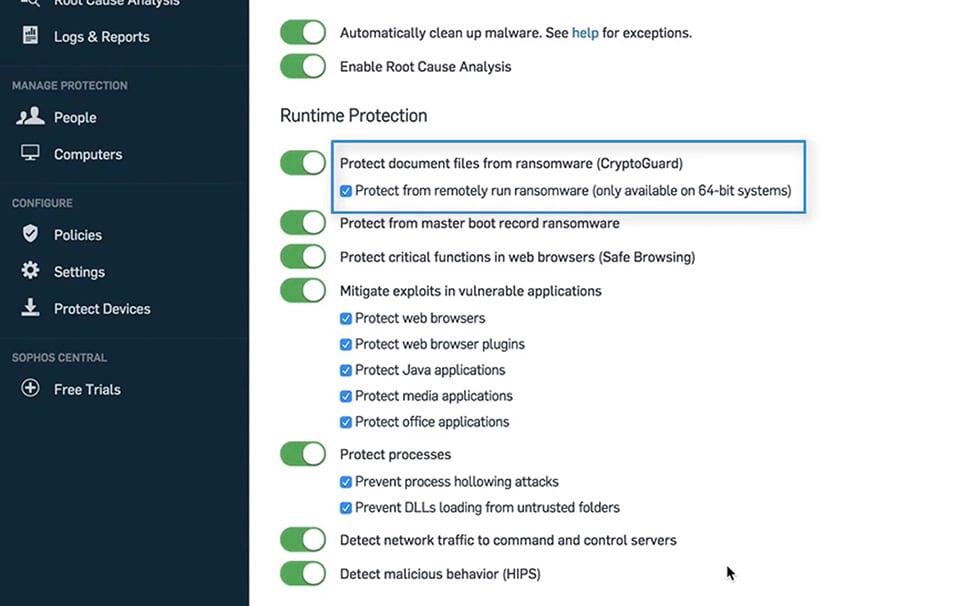
Today’s ransomware attacks often combine multiple advanced techniques with real-time hacking. To minimize your risk of falling victim you need advanced protection that monitors and secures the whole attack chain. Sophos Intercept X for Server gives you advanced protection capabilities that disrupt the whole attack chain including deep learning that predictively prevents attacks and CryptoGuard which rolls back the unauthorized encryption of files in seconds.
Server Lockdown & File Integrity Monitoring
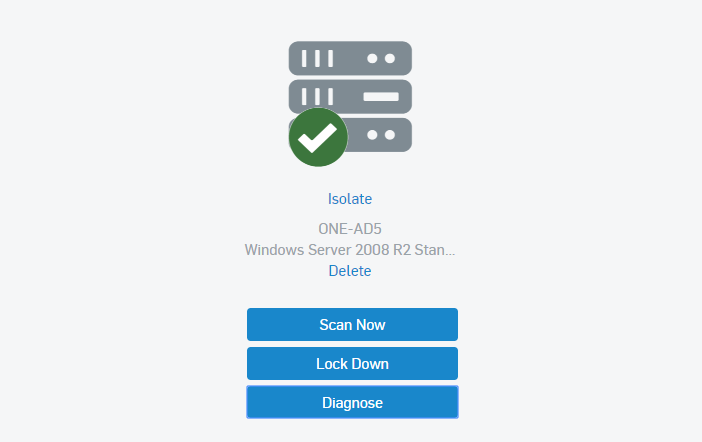
Server Lockdown (whitelisting) ensures that only the applications you want on your servers can be run. It only takes a single click and it doesn’t require server downtime. File integrity monitoring (FIM) notifies you if attempts are made to tamper with critical files.
Linux Detection
When uptime is your no.1 requirement, security tools must be lightweight and integrate into your DevSecOps workflows to prevent risk and optimize application performance. Sophos protection for Linux identify sophisticated attacks as they happen without requiring a kernel module, orchestration, baselining, or system scans. Avoiding costly downtime, overloaded hosts, or stability snafus caused by traditional security tools with a single agent with optimized resource limits (including CPU, memory, and data collection limits).
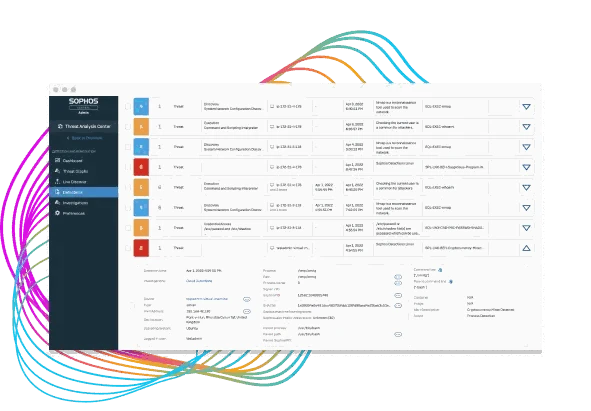
Minimize Time to Detect and Respond
Sophos Cloud Workload Protection provides complete visibility into your host and container workloads, identifying malware, exploits, and anomalous behavior before they get a foothold.
- Extended detection and response (XDR) provides complete visibility of hosts, containers, endpoints, the network, and even cloud provider native services
- Cloud-native behavioral and exploit runtime detections identify threats including container escapes, kernel exploits, and privilege escalation attempts
- Streamlined threat investigation workflows prioritize high-risk incident detections and consolidate connected events to increase efficiency
- Integrated Live Response establishes a secure command line terminal to hosts for remediation
Container Security
Behavioral and exploit runtime detections identify threats including container escapes, kernel exploits, and privilege escalation.
Share